Being worried about passing your 70-663 exam? Why not trying PassLeader’s 70-663 VCE or PDF dumps? We PassLeader now are offering the accurate 291q 70-663 exam questions and answers, you can get all the real exam questions from our 70-663 exam dumps. All our 291q 70-663 practice tests are the newest and same with the real test. We ensure that you can pass 70-663 exam easily with our premium 70-663 study guide! Now visit passleader.com to get the valid 70-663 braindumps with free version VCE Player!
keywords: 70-663 exam,291q 70-663 exam dumps,291q 70-663 exam questions,70-663 pdf dumps,70-663 vce dumps,70-663 braindumps,70-663 practice test,70-663 study guide,Pro: Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Exam

QUESTION 16
You have an Exchange organization that consists of the servers shown in the following table. You plan to implement moderated transport for distribution groups in the organization. You need to recommend changes to the organization to support the planned implementation. What should you recommend?
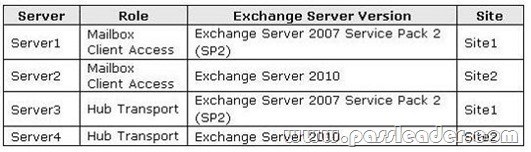
A. Upgrade Server 3 to Exchange Server 2010.
B. Install Windows Server 2008 R2 global catalog servers.
C. Replace all distribution groups with dynamic distribution groups.
D. Use Server4 as the expansion server for all moderated distribution groups.
Answer: D
Explanation:
Using the moderated transport feature in Microsoft Exchange Server 2010, you can require all e-mail messages sent to specific recipients be approved by moderators. Exchange 2010 Hub Transport servers will ensure that all messages sent to those recipients go through an approval process. Moderation must be done on a Exchange 2010 Hub Transport Server [as this is a new feature in 2010]. Before you make heavy use of moderated distribution lists, you should make sure that the message doesn’t have to pass through any non-Exchange 2010 Hub Transport servers. Older Hub Transport servers will simply pass messages on to group members and ignore moderation options. You enable moderation features on an existing distribution group. Go to groups Properties, then Mail Flow Settings, then Message Moderation.
QUESTION 17
You have an Exchange Server 2010 organization. You need to recommend an e-mail retention solution to meet the following requirements:
– Ensure that users can manually control the expiration of messages in their inbox folders
– Ensure that administrators can archive messages that are older than a specified number of days automatically
What should you recommend?
A. managed folders
B. journal rules
C. Personal Archives
D. Retention policies
Answer: D
QUESTION 18
Your network contains two Exchange Server 2010 Edge Transport servers. The network also contains five Hub Transport servers in two Active Directory sites. All e-mail send to the network in received by the Edge Transport servers. You plan to configure anti-spam filtering. You need to ensure that the anti-spam filtering configurations are applied to both Edge Transport servers. The solution must use a minimum amount of administrative effort. What should you do?
A. Configure EdgeSync synchronization
B. Implement Active Directory Federation Services (AD FS)
C. Join both Edge Transport servers to an Active Directory domain and then create a forest trust for the internal forest
D. Manually configure settings on one Edge Transport server and then export the settings to the other Edge Transport server
Answer: D
Explanation:
You can use the provided Shell scripts to duplicate the configuration of a computer that has the Microsoft Exchange Server 2010 Edge Transport server role installed. This process is referred to as cloned configuration. Cloned configuration is the practice of deploying new Edge Transport servers based on the configuration information from a previously configured source server. The configuration information from the previously configured source server is copied and exported to an XML file, which is then imported to the target server.
ExportEdgeConfig.ps1. This script exports all user-configured settings and data from an Edge Transport server and stores that data in an XML file.
ImportEdgeConfig.ps1. During the validate configuration step, the ImportEdgeConfig.ps1 script checks the XML file to see whether the server-specific export settings are valid for the target server. If settings have to be modified, the script writes the invalid settings to an answer file that you modify to specify the target server information that’s used during the import configuration step. During the import configuration step, the script imports all user- configured settings and data that’s stored in the intermediate XML file that was created by the ExportEdgeConfig.ps1 script.
QUESTION 19
You have an Exchange Server 2010 organization. You plan to deploy a monitoring solution for Exchange Server 2010. You need to recommend a solution to track the usage of ActiveSync clients and to analyze usage trends. What should you include in the solution?
A. Internet Information Server log files
B. Exchange Server Mail Flow Troubleshooter
C. Exchange Server Performance Troubleshooter
D. Microsoft System Control Configuration Manager
Answer: A
QUESTION 20
You have an Exchange Server 2010 organization. You plan to deploy a public folder access solution to meet the following requirements:
– Users in the legal department must be able send e-mail messages to public folders
– Users in the legal department must not be able to read documents in the public folders by using Outlook Web App (OWA)
You need to recommend changes to public folder access that meet the company requirements. What should you recommend?
A. mail-enabled public folders and Editor Permissions
B. mail-enabled public folders and Contributor permissions
C. OWA segmentation and Reviewer permissions
D. OWA segmentation and Send As permissions
Answer: B
Explanation:
Public folders are only required in Exchange 2010 if you:
1. Have the requirement to support Outlook 2003 clients,which cannot use web-based distribution to access OAB and free/busy data. Outlook 2007 clients are also able to use public folders in this way but Outlook 2010 clients only use web-based distribution to access OAB and free/busy data.
2. Have applications that are based on public folders. Ten years ago, these applications were reasonably popular but recently they have become a fast-disappearing category as companies have migrated applications to more modern and functional platforms. SharePoint and InfoPath forms are an option that is often considered for the kind of forms- based applications that were deployed on top of public folders.
QUESTION 21
Your network consists of a single Active Directory domain. The domain contains three domain controllers and one DNS server. You plan to deploy Exchange Server 2010. You need to recommend a DNS implementation that provides redundancy if a DNS server fails. What should you include in the recommendations?
A. Active Directory integrated DNS server
B. DNS forwarding
C. integrated DNS and WINS
D. multiple MX records
Answer: A
Explanation:
With 3 domain controller all running the DNS service this will provide good fault tolerance if a single server fails. Keep in mind that Exchange Server also requires Global Catalog Servers – so you should have more than one on the network.
QUESTION 22
Your company has three offices. Each office has a direct link to the Internet. The offices connect to the each other by using a WAN link. Your network consists of an Active Directory forest that contains two domains and one site. The functional level of the forest is windows server 2003. All domains controllers run Windows Server 2003 R2. Each office contains two domains controllers for each domain. All domain controllers are global catalog servers. In each office, you plan to deploy Mailbox, Client Access and Hub Transport Exchange Server 2010 servers. All e-mail messages sent to the Internet will be delivered from a local server in each office. You need to recommend changes to the Active Directory environment to support the planned deployment of Exchange Server 2010. What should you recommend?
A. Disable site link building for the forest.
B. Modify the cost values for the default IP site link.
C. Create a separate Active Directory subnet and site object for each office.
D. Upgrade one domain controller in each office to windows Server 2008.
Answer: C
Explanation:
Internal message routing is based on the AD site architecture.

http://www.passleader.com/70-663.html
QUESTION 23
You have an Exchange Server 2010 organization and an Active Directory Rights Management Services (AD RMS) server. All users access their mailboxes by using Outlook Web App (OWA). You need to plan a security solution for the organization to meet the following requirements:
– Secure messages by using administrator-defined templates
– Ensure that e-mail messages sent by users can be stored in an encrypted format
What should you include in the plan?
A. a legal hold
B. Domain Security
C. Outlook Protection Rules
D. Secure/Multipurpose Internet Mail Extensions (S/MIME)
Answer: C
Explanation:
Information workers exchange sensitive information such as financial reports and data, customer and employee information, and confidential product information and specifications, by e-mail everyday. In Microsoft Exchange Server 2010, Microsoft Outlook, and Microsoft Office Outlook Web App, users can apply Information Rights Management (IRM) protection to messages by applying an Active Directory Rights Management Services (AD RMS) rights policy template. This requires an AD RMS deployment in the organization. For more information about AD RMS, see Active Directory Rights Management Services. However, when left to the discretion of users, messages may be sent in clear text without IRM protection. In organizations that use e-mail as a hosted service, there’s a risk of information leakage as a message leaves the client and is routed and stored outside the boundaries of an organization. Although e-mail hosting companies may have well-defined procedures and checks to help mitigate the risk of information leakage, after a message leaves the boundary of an organization, the organization loses control of the information. Outlook protection rules can help protect against this type of information leakage. In Exchange 2010, Outlook protection rules help your organization protect against the risk of information leakage by automatically applying IRM-protection to messages in Outlook 2010. Messages are IRM-protected before they leave the Outlook client. This protection is also applied to any attachments using supported file formats. When you create Outlook protection rules on an Exchange 2010 server, the rules are automatically distributed to Outlook 2010 by using Exchange Web Services. For Outlook 2010 to apply the rule, the AD RMS rights policy template you specify must be available on users’ computers.
QUESTION 24
You have an Exchange Server 2010 organization. You design a deployment of multiple Mailbox servers. Your company’s Service Level Agreement (SLA) states that servers must support 1,000 concurrent connections to mailboxes while maintaining an ——- latency of less than 20 milliseconds. You need to verify that your design meets the requirements of the SLA before you deploy servers in the production environment. Which tool should you use?
A. Exchange Server Jetstress 2010
B. Exchange Server User Monitor (ExMon)
C. Exchange Server Load Generator (LoadGen) 2010
D. Exchange Server Remote Connectivity Analyzer (ExRCA)
Answer: C
Explanation:
Use Microsoft Exchange Load Generator (LoadGen) as a simulation tool to measure the impact of MAPI, OWA, IMAP, POP and SMTP clients on Exchange servers. LoadGen allows you to test how a server running Exchange responds to e-mail loads. To simulate the delivery of these messaging requests, you run LoadGen tests on client computers. These tests send multiple messaging requests to the Exchange server, thereby causing a mail load. LoadGen is a useful tool for administrators who are sizing servers and validating a deployment plan. Specifically, LoadGen helps you determine if each of your servers can handle the load to which they are intended to carry. Another use for LoadGen is to help validate the overall solution.
http://www.microsoft.com/download/en/details.aspx?id=14946
QUESTION 25
Your company has an Active Directory forest. The network contains Exchange Server 2007 Service Pack 1 (SP1) and Exchange Server Service Pack 2 (SP2) servers. All domain controllers run windows Server 2003 Service Pack 1 (SP1). You plan to deploy Exchange Server 2010 on the network. You need to recommend changes to the servers so that you can deploy Exchange Server 2010 servers. What should you upgrade first?
A. all domain controllers to Windows Server 2003 (x64) SP2
B. all domain controllers to Windows Server 2008 (x86)
C. all Exchange Server 2003 servers to Exchange Server 2007 SP2
D. all Exchange Server 2007 SP1 servers to Exchange Server 2007 SP2
Answer: D
Explanation:
Exchange Server 2007 Service Pack 2 (SP2) sets the foundation for the transition to Exchange Server 2010. SP2 includes the usual fixes and updates, and also functionality that will allow Exchange Server 2007 and Exchange Server 2010 to coexist.
QUESTION 26
Your network contains 20 offices. Each office contains 1,000 users. The users access their e-mail messages by using Microsoft Exchange server. You have an Exchange Server 2010 organization. You need to recommend an Exchange Server solution that meets the following requirement:
– Ensures that users in each office download the list of recipients for their office only
– Ensures that users in each office can send e-mail messages to any user in the organization
What should you recommend?
A. Create 20 new address lists and 20 offline address books (OABs).
B. Create 20 new managed folder mailbox policies and 20 e-mail address policies.
C. Create 20 new dynamic distribution groups and then create 20 new global address lists (GALs).
D. Create 20 new mailbox databases and then move the mailboxes from each office to a separate mailbox database.
Answer: A
Explanation:
Address lists are a collection of recipient and other Active Directory objects. Each address list can contain one or more types of objects (for example, users, contacts, groups, public folders, conferencing, and other resources). Address lists also provide a mechanism to partition mail-enabled objects in Active Directory for the benefit of specific groups of users. When Outlook users are running in cached mode or otherwise disconnected from their Exchange infrastructure, they rely on the Offline Address Book (OAB) to provide them with access to one or more address lists that are always available when they are connected directly to Exchange. It’s the Microsoft Exchange System Attendant service running on the mailbox server role that first produces the OAB data. But the distribution is done by CAS web server [OAB virtual directory]. The specific mailbox server that produces the initial data depends on which server has been configured to generate the OAB.
QUESTION 27
You have an Exchange Server 2010 organization that contains a database availability group (DAG). You need to recommend a Mailbox database security solution to meet the following requirements:
– Maximize read/write performance
– Prevent access to database files if a server is stolen
What should you recommend?
A. Encrypted File System (EFS)
B. DAG network encryption
C. Rights Management Service (RMS)
D. Windows BittLocker Drive Encryption
Answer: D
QUESTION 28
You have an Exchange Server 2010 organization. You have a global security group named Legal that contains all the members of your company’s legal department. The company’s security policy states that the Legal group must be able to search all mailboxes for e-mail messages that contain specific keywords. You need to recommend a solution for the organization that complies with the security policy. What should you include in the solution?
A. a Discovery Management role group
B. a legal hold
C. administrator audit logging
D. Mailbox journaling
Answer: A
Explanation:
http://technet.microsoft.com/en-us/library/dd351080.aspx
QUESTION 29
You have an Exchange Server 2010 organization. Your company’s compliance policy states the following:
– Delete e-mail messages sent to legal department users that are older than 180 days.
– Delete e-mail messages sent to all other uses that are older than 60 days.
You need to recommend a solution that meets the requirements of the compliance policy. What should you recommend?
A. Configure deleted item retention for all users.
B. Configure Personal Archives for legal department users.
C. Create two Managed Folder mailbox policies. Use one policy for the legal department users. Use the other policy for all other users.
D. Create two new message classifications. Use one messages classification for the e-mail sent to legal department users. Use the other message classification for the e-mail sent to all other users.
Answer: C
QUESTION 30
You have an Exchange Server 2010 organization. The users access their mailboxes by using Outlook Web App (OWA). You need to plan a solution to reduce the number of e-mail messages that are accidentally sent to distribution groups that contain company executives. What should you include in the plan?
A. custom MailTips
B. dynamic distribution groups
C. Outlook Protection Rules
D. sharing policies
Answer: A
Explanation:
MailTips are informative messages displayed to users while they’re composing a message. Microsoft Exchange Server 2010 analyzes the message, including the list of recipients to which it’s addressed, and if it detects a potential problem, it notifies the user with MailTips prior to sending the message. With the help of the information provided by MailTips, senders can adjust the message they’re composing to avoid undesirable situations or non- delivery reports (NDRs). The following unproductive messaging scenarios are common in any messaging environment:
NDRs resulting from messages that violate restrictions configured in an organization such as message size restrictions or maximum number of recipients per message.
NDRs resulting from messages sent to recipients that don’t exist, recipients that are restricted, or users whose mailboxes are full. Sending messages to users with Automatic Replies configured. All of these scenarios involve the user sending a message, expecting it to be delivered, and instead receiving a response stating that the message isn’t delivered. Even in the best-case scenario, like the automatic reply, these events result in lost productivity. In the case of an NDR, this scenario could result in a costly call to the Help desk.
There are also several scenarios where sending a message won’t result in an error, but can have undesirable, even embarrassing consequences:
Messages sent to extremely large distribution groups. Messages sent to inappropriate distribution groups. Messages inadvertently sent to recipients outside your organization. Selecting Reply to All to a message that was received as a Bcc recipient. All of these problematic scenarios can be mitigated by informing users of the possible outcome of sending the message as they’re composing the message. For example, if senders know that the size of the message they’re trying to send exceeds the corporate policy, they won’t attempt to send the message. Similarly, if senders are notified that the message they’re sending will be delivered to people outside the organization, they’re more likely to ensure that the content and the tone of the message are appropriate.
By addressing the scenarios listed earlier, MailTips can help you to:
Reduce the cost of processing and storing messages by preventing NDRs. Reduce the volume of Help desk calls caused by NDRs. Increase productivity by avoiding communications that won’t succeed, for example, breaking the cycle of sending an e-mail message, receiving an automatic reply, and then redirecting the message.
Inform your users as they compose e-mail messages about various policies configured in your organization that impose limits on the messages sent. Direct your users to the correct distribution groups. Reduce the risk of inadvertent disclosure of information to people outside your organization.
http://technet.microsoft.com/en-us/library/dd297974.aspx

http://www.passleader.com/70-663.html