How To Pass The New 70-642 Exam? PassLeader now is offering the newest and 100 percent pass ensure 70-642 exam dumps with free pdf and vce dumps download, the latest updated 448q 70-642 exam questions are the most accurate exam dumps with all new questions including, which will help you passing 70-642 exam easily and quickly. Now visit our site passleader.com and get the valid 448q 70-642 vce and pdf practice test and FREE VCE PLAYER!
keywords: 70-642 exam,448q 70-642 exam dumps,448q 70-642 exam questions,70-642 pdf dumps,70-642 vce dumps,70-642 braindumps,70-642 practice tests,70-642 study guide,TS: Windows Server 2008 Network Infrastructure, Configuring Exam

QUESTION 51
Your company has a single Active Directory domain named contoso.com. All servers run Windows Server 2008. You have a public DNS server named Server1, and an e-mail server named Server2. Client computers outside the company domain are unable to send e-mail messages to contoso.com You verify that the host (A) DNS record for Server2 is availible to external client computers. You need to ensure Server2 can receive e-mail messages from external client computers. How should you configure the contoso.com DNS zone?
A. Add a Mail Exchange (MX) record for Server2
B. Add a Mailbox (MB) record for Server2. Set the Mailbox Host setting to Server2
C. Add a Canonical (CNAME) record that maps Server2 to contoso.com
D. Add a Service Locator (SRV) record for Server2. Set the Service field to _smtp. Set the Protocol field to _tcp. Set the Port Number to 25
Answer: A
QUESTION 52
Your company has a domain controller that runs Windows Server 2008 and the DNS role. The DNS domain is named contoso.com You need to ensure that inquries about contoso.com are sent to [email protected] What should you do?
A. Create a signature (SIG) record for the domain controller
B. Modify the Name Server (NS) record for the domain controller
C. Modify the Service Locator (SRV) record for the domain controller
D. Modify the Start of Authority (SOA) record ont he domain controller
Answer: D
QUESTION 53
Your company has servers that run Windows Server 2008. All client computers run Windows XP Service Pack 2 (SP2). Windows 2003 Professional, or Windows Vista. You need to ensure all computers can use the IPv6 protocol. What should you do
A. Install Serivce Pack 4 on all Windows 2000 Professional computers
B. Upgrade the Windows 2000 professional computers to Windows XP SP2
C. Run the IPv6.exe tool on the Windows 200 Professional and Windows XP computers
D. Install Active Directory Client extention (DSClient.exe) on the Windows 2000 Professional and Windows XP computers
Answer: B
QUESTION 54
Your company has a single Active Directory domain. All servers run Windows Server 2008. The company network has servers that perform as Web Servers. All confidential files are located on a server named FSS1. The company security policy states that all confidential data must be transmitted in the most secure manner. When you monitor the network you notice that the confidential files stored on FSS1 server are being transmitted over the network without encryption. You need to ensure that encryption is always used when the confidential files on the FSS1 server are transmitted over the network. What are two possible ways to achieve this goal? (Each correct answer presents a complete solution. Choose two.)
A. Deactivate all LM and NTLM authentication methods on FSS1 server
B. Use IIS to publish the confidential files, activate SSL on the IIS server, and then open the files as a web folder
C. Use IPsec encryption between the FSS1 server and the computers of the users who need to access the confidential files.
D. Use the Server Message Block (SMB) signing between the FSS1 server and the computers of the users who want to access the confidential files.
E. Activate offline files for the confidential files that are stored on the FSS1 server. In the Folder Advanced Properties box, select the Encrypt contents to secure data optiion
Answer: BC
QUESTION 55
Your company has an Active Directory domain. Aserver named Server1 runs the Network Access Policy server role. You need to disable IPv6 for all connections except for the tunnel interface and the IPv6 Loopback interface. What should you do?
A. Run the netsh ras ipv6 set command
B. Run the netsh interface ipv6 delete command
C. Run ipv6.exe and remove the IPv6 Protocol
D. From the Local Area Connection Properties, uncheck Internet Protocol Version 6 (TCP/IPv6)
Answer: D
QUESTION 56
Your company has a single Active Directory domain. The domain runs at the functional level of Windows Server 2003. You install the DHCP service on a server named DHCP1. You attempt to start the DHCP service, but it does not start. You need to ensure that the DHCP service starts. What should you do?
A. Restart DHCP1
B. Configure a scope on DHCP1
C. Activate the scope on DHCP1
D. Authorize DHCP1 in the Active Directory domain
Answer: D
QUESTION 57
You configure a new file server that runs Windows Server 2008. Users access shared files on the file server. Users report that they are unable to access the shared files. The TCP/IP properties for the file server are configured as shown in the following exhibit.
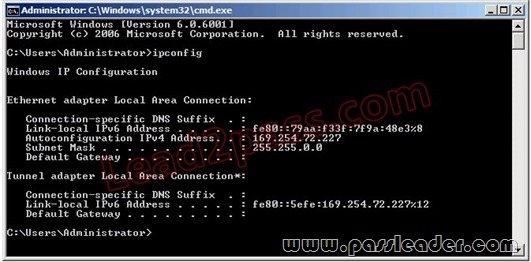
You need to ensure that users are able to access the shared files. How should you configure the TCP/IP properties in the file server?
A. Configure a static IP address
B. Configure the default gateway
C. Configure the DNS server address
D. Add the domain to the DNS suffix on the network interface
Answer: A
QUESTION 58
Your company has Active Directory Certificate Services (AD CS) and Network Access Protection (NAP) deployed on the network. You need to configure the wireless network to accept smart cards. What should you do?
A. Configure the wireless network to use WPA2, PEAP, and MSCHAP v2
B. Configure the wireless network to use WPA2, 802.1X authentication and EAP-TLS
C. Configure the wireless network to use WEP, 802.1X authentication, PEAP, and MSCHAP v2
D. Configure the wireless network to use WPA, PEAP, and MSCHAP v2 and also require strong user passwords
Answer: B
QUESTION 59
Your company has users who connect remotely to the main office though a Windows Server 2008 VPN server. You need to ensure that users cannot access the VPN server remotely from 22:00 to 05:00. What should you do?
A. Create a network policy for VPN connections. modify the Day and time restrictions.
B. Create a network policy for VPN connections. apply an ip filter to deny access to the corporate network.
C. Modify the Logon hours for all users objects to specify only the VPN server otn he computer restrictions option
D. Modify the Logon hours for the default domain policy to enable the Force logoff when logon hours expire option.
Answer: A
QUESTION 60
You have a server that runs Windows Server 2008. You need to configure the server as a VPN server. What should you installed on the server?
A. Windows Deployment Serivces role and Deployment Server role service.
B. Windows Deployment Services role and Deployment Transport Role Service.
C. Network Policy and Access Services role and Routing and Remote Access Services role service.
D. Network Policy and Access Services role and Routing and Host Credential Authorization Protocolr ole service.
Answer: C

http://www.passleader.com/70-642.html
QUESTION 61
You manage a server that runs Windows Server 2008 R2. The D:\Payroll folder is corrupted. The most recent backup version is 10/29/2007-09:00. You need to restore all the files in the D:\Payroll folder back to the most recent backup version without affecting other folders on the server. What should you do on the server?
A. Run the Recover d:\payroll command.
B. Run the Wbadmin restore catalog -backuptarget:D: -version:10/29/2007-09:00 -quiet command.
C. Run the Wbadmin start recovery -backuptarget:D: -version:10/29/2007-09:00 -overwrite -quiet command.
D. Run the Wbadmin start recovery -version:10/29/2007-09:00 -itemType:File -items:d:\Payroll – overwrite – recursive -quiet command.
Answer: D
QUESTION 62
Your company has a server named Server1 that runs Windows Server 2008 R2. The Windows Server Backup feature is installed on Server1. Server1 fails. You install a new server named Server2 that runs Windows Server 2008 R2. You need to restore the company’s Windows SharePoint Services (WSS) site to Server2. What should you do?
A. Use Wbadmin to restore the system state from backup.
B. Run Wbadmin with the Get Versions option. Install WSS.
C. Run Wbadmin with the Start Recovery option. Install WSS.
D. Use Wbadmin to restore the application and the sites from backup.
Answer: D
QUESTION 63
You have a server that runs Windows Server 2008 R2. You create a new quota template. You apply quotas to 100 folders by using the quota template. You need to modify the quota settings for all 100 folders. You must achieve this goal by using the minimum amount of administrative effort. What should you do?
A. Modify the quota template.
B. Delete and recreate the quota template.
C. Create a new quota template. Modify the quota for each folder.
D. Create a file screen template. Apply the file screen template to the root of the volume that contains the folders.
Answer: A
QUESTION 64
You have a file server that runs Windows Server 2008 R2. You configure quotas on the server. You need to view each user’s quota usage on a per folder basis. What should you do?
A. From File Server Resource Manager, create a File Screen.
B. From File Server Resource Manager, create a Storage Management report.
C. From the command prompt, run dirquota.exe quota list.
D. From the properties of each volume, review the Quota Entries list.
Answer: B
QUESTION 65
Your company has a server named SRV1 that runs Windows Server 2008 R2. The default Print Services server role is installed on SRV1. The company wants to centralize printing on SRV1 for both UNIX and Windows users. You need to provide support to the UNIX users who print on SRV1. What are two possible ways to achieve this goal? (Each correct answer presents a complete solution.Choose two.)
A. Install the Internet Printing role service on SRV1.
B. Install the Line Printer Daemon (LPD) Services role service on SRV1.
C. Configure the printers on SRV1 to use Line Printer Remote printing.
D. Install the File Services server role on SRV1 and activate the Services for Network File System role service.
Answer: AB
Explanation:
Line Printer Daemon (LPD) – A service on a print server that receives print jobs from Line Printer Remote (LPR) tools that are running on client computers.
Internet Printing Protocol (IPP) – The protocol that uses the Hypertext Transfer Protocol (HTTP) to send print jobs to printers throughout the world.
http://technet.microsoft.com/en-us/library/cc783789(v=ws.10).aspx
QUESTION 66
Your company has a main office and one branch office. The main office has a print server named Printer1. The branch office has a print server named Printer2. Printer1 manages 15 printers and Printer2 manages seven printers. You add Printer2 to the Print Management console on Printer1. You need to send an automatic notification when a printer is not available. What should you do?
A. Configure an e-mail notification for the Printers With Jobs printer filter.
B. Configure an e-mail notification for the Printers Not Ready printer filter.
C. Enable the Show informational notifications for local printers option on both print servers.
D. Enable the Show informational notifications for network printers option on both print servers.
Answer: B
QUESTION 67
Your company has a server named Printer1 that runs Windows Server 2008 R2. Printer1 has the Print and Document Services server role installed. You need to reduce the number of events registered in the system log on Printer1. What should you do?
A. Open the Event Viewer console. Create a custom view for the system log. Exclude the events that are notified by Event ID 10 from the filter.
B. Open the Print Management console. Open the properties of Printer1 and clear the Log spooler information events option.
C. Open the Print Management console. Open the properties of Printer1 and clear the Show informational notifications for network printers option.
D. Open the Print Management console. Open the properties of each individual printer on Printer1 and clear the Enable advanced printing features option.
Answer: B
QUESTION 68
Your company runs Windows Server Update Services (WSUS) on a server named Server1. Server1 runs Windows Server 2008 R2. Server1 is located on the company intranet. You configure the WSUS Web site to use SSL. You need to configure a Group Policy object (GPO) to specify the intranet update locations. Which URLs should you use?
A. http: //SERVER1
B. http: //SERVER1:8080
C. https: //SERVER1
D. https: //SERVER1:8080
Answer: C
QUESTION 69
You have 10 standalone servers that run Windows Server 2008 R2. You install the Windows Server Update Services (WSUS) server role on a server named Server1. You need to configure all of the servers to receive updates from Server1. What should you do?
A. Configure the Windows Update settings on each server by using the Control Panel.
B. Run the wuauclt.exe /detectnow command on each server.
C. Run the wuauclt.exe /reauthorization command on each server.
D. Configure the Windows Update settings on each server by using a local group policy.
Answer: D
QUESTION 70
Your network consists of a single Active Directory domain. All servers run Windows Server 2008 R2. You have a server named Server1 that hosts shared documents. Users report extremely slow response times when they try to open the shared documents on Server1. You log on to Server1 and observe real-time data indicating that the processor is operating at 100 percent of capacity. You need to gather additional data to diagnose the cause of the problem. What should you do?
A. In the Performance Monitor console, create a counter log to track processor usage.
B. In Event Viewer, open and review the application log for Performance events.
C. In Resource Monitor, use the Resource View to see the percentage of processor capacity used by each application.
D. In Performance Monitor, create performance counter alert that will be triggered when processor usage exceeds 80 percent for more than five minutes on Server1.
Answer: C

http://www.passleader.com/70-642.html